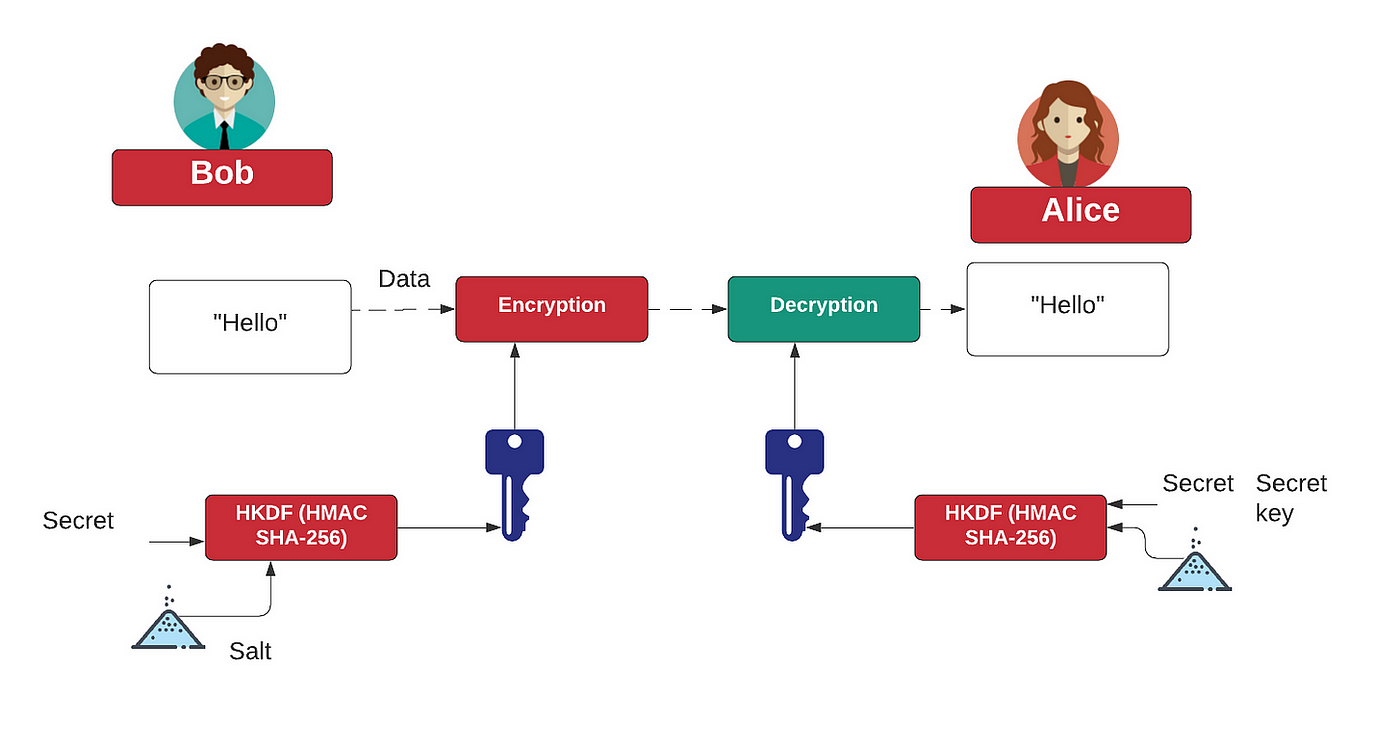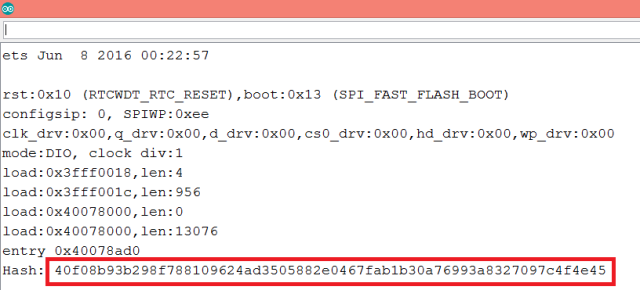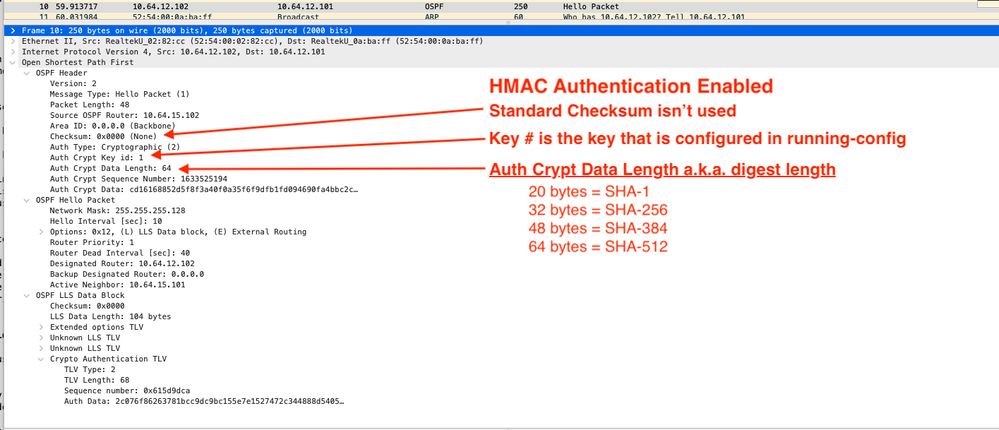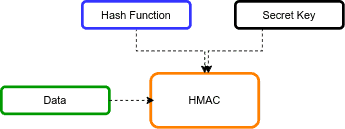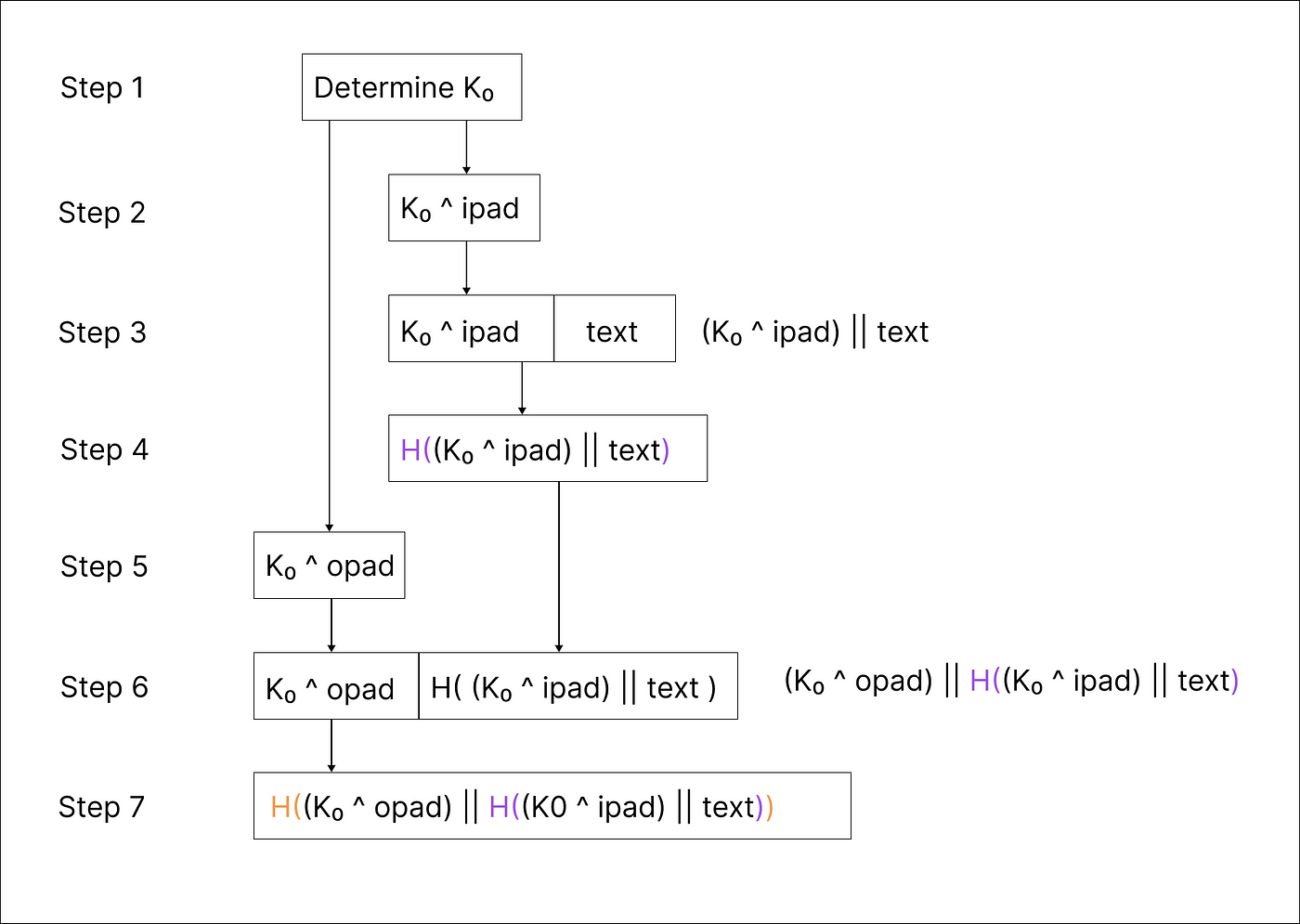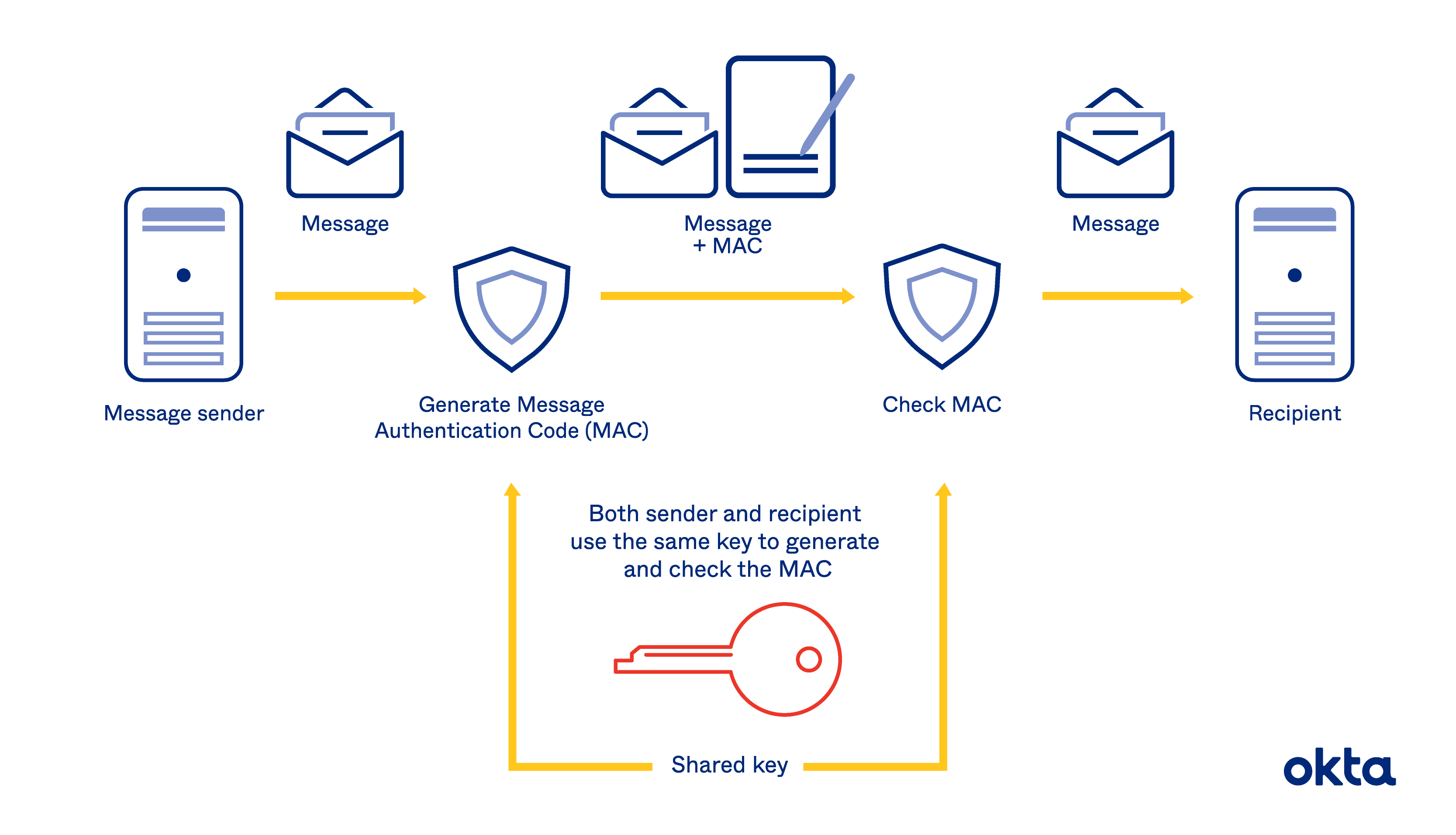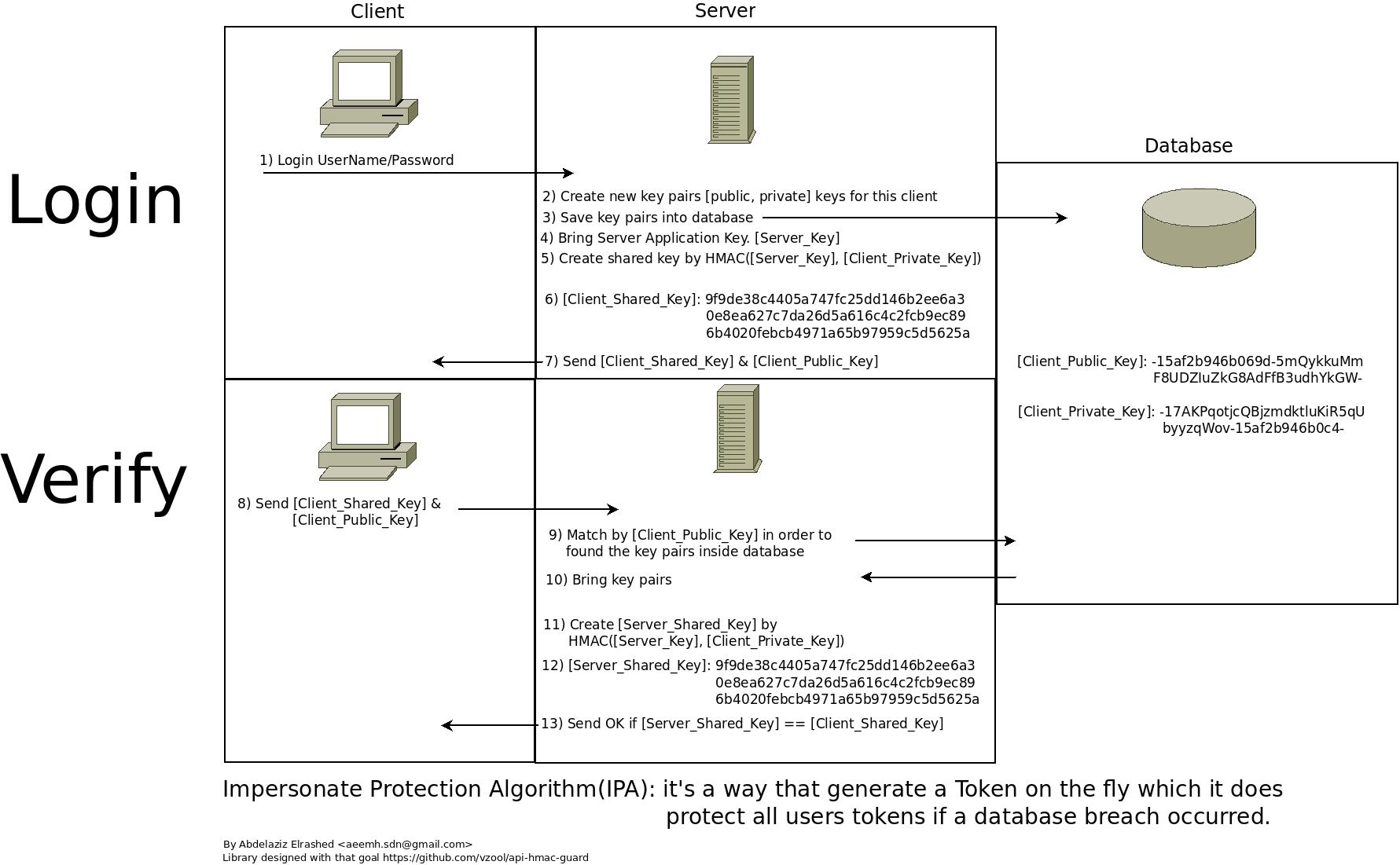
GitHub - vzool/api-hmac-guard: A simple and secure way of authenticating your RESTful APIs with HMAC keys using Laravel

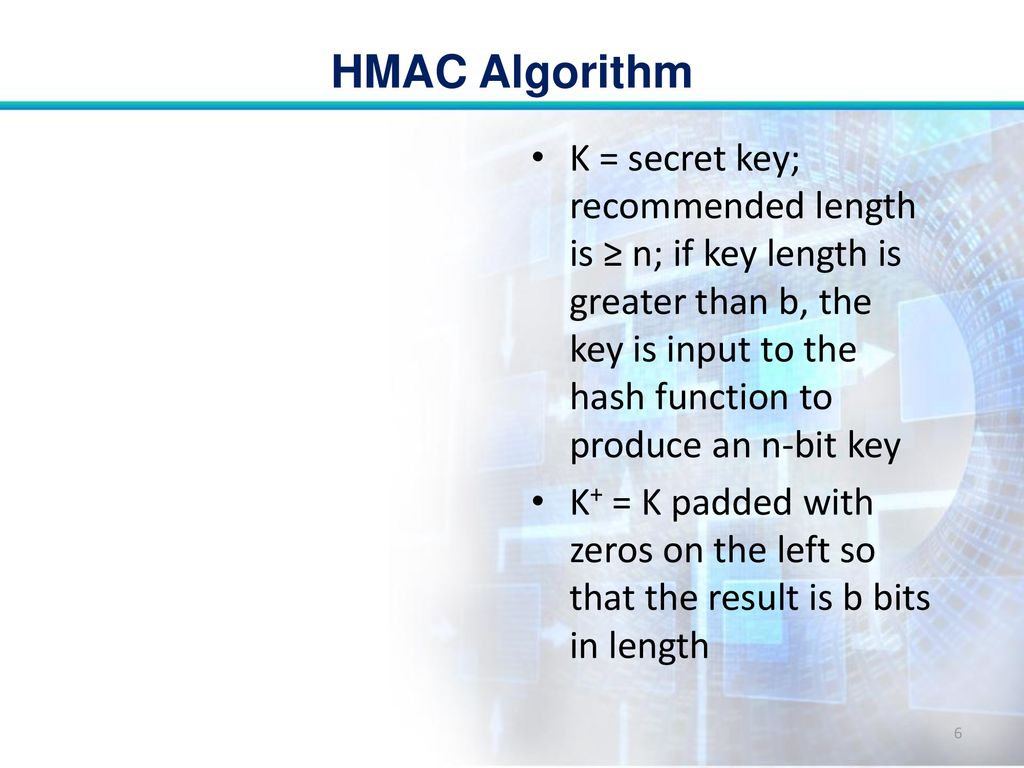
What is a size of mac_length and mac_key_length for TLS cipher suites HMAC using SHA384 and SHA512? - Cryptography Stack Exchange